Cyber-crime: India
This is a collection of articles archived for the excellence of their content. the Facebook community, Indpaedia.com. All information used will be acknowledged in your name. |
PART I
Action on complaints received
2022-23
V Narayan, June 26, 2023: The Times of India

From: V Narayan, June 26, 2023: The Times of India
Mumbai: Under 1% of cyber offences in Maharashtra resulted in an FIR out of the 195,409 online complaints received on the National Cyber Crime Reporting Portal from January 2022 to May 2023. According to a Right to Information (RTI) plea obtained by activist Jeetendra Ghadge, only two percent (42,868) of a total of 2,099,618 cyber-related complaints received on the portal from all states during the period were converted into FIRs. Among 27 states, including Maharashtra, the FIR registration rate was below 1% (just 0. 8%).
The RTI dat a revealed that Delhi received 216,739 complaints, with 1. 2% resulting in FIRs. Telangana stood out as an exception, registering the highest number of FIRs at 17%. Meghalaya followed with 8% FIR registration, while Assam and Tamil Nadu had rates of 2. 7% and 2. 2%, respectively. Former police officers expressed their belief that the cybercrime department lacked sufficient in spectors to register cases. Cyber experts emphasized that the low rate of filed FIRs in cybercrime cases undermines public trust in law enforcement.
Experts acknowledged the steps taken by the Union government in combating cybercrime with the introduction of the National Cyber Crime Reporting Portal. But its use is limited when it comes to registering cases. The initiative aims to empower victims and complainants by providing them with a convenient platform to report cybercrime complaints online. The portal covers a wide range of cybercrime, including online child pornography, child sexual abuse material, sexually explicit content such as rape/gang rape (CP/ RGR), mobilephone crime, online and social media crime, online financial fraud, ransomware, hacking, crypto currency crime, and online cyber trafficking.
RTI activist Jeetendra Ghadge of The Yo u ng Whistleblowers Foundation said, “The portal makes it easy for citizens to register complaints. But the lack of FIR registrations by state governments limits its effectiveness. Given rapid technological advancements and evolving crime patterns, it is crucial for the central and state governments to collaborate on a solution to comb at the growing menace of cybercrime. ”
Former Mumbai police commissioner D Sivanandhan pointed out that as per Section 76 of the IT Act 2000 only police officers of rank inspector and above can in- vestigate cyber cases. “We do not have enough inspectors to register cases. Furthermore, not all inspectors are tech-savvy enough to conduct investigations. Additionally , we lack the necessary hardware and software to handle such a monumental task,” he said.
Cyber lawyer Prashant Mali criticised “inaction of the state government”. “It allows cybercriminals to loot Mumbai without even freezing the stolen funds when they are in banks. It seems that Mumbaikars are easy targets for cybercriminals across the country, and the government's inaction facilitates their crimes,” he said.
Cyber expert Ritesh Bhatia emphasised the importance of addressing the low rate of filed FIRs in cyber fraud cases, as it undermines public trust in law enforcement.
Ghadge stated that while the portal serves as a vital channel for reporting cybercrime, its primary role is that of an intermediary, forwarding the complaints to the respective states and Union territories for necessary police action since the jurisdiction of the police machinery falls under the purview of the state governments.
Cost of Cybercrimes to the nation
2013: Surinder S Rathi's report to the Delhi High Court
Cybercrimes alone cost India Rs 24,630 crore in 2013: Report
PTI | Jul 6, 2014
It said that in Delhi alone, a total of 86,800 criminal complaints were received at its 175 odd police stations.
NEW DELHI: Cyber crimes have cost India a whopping about Rs 24,630 crore ($4 billion) in 2013 alone as criminals used sophisticated means, says a Delhi High Court-commissioned report.
"Internet frauds alone have cost India a whopping $4 billion (about Rs 24,630 crore) in 2013 as cyber criminals are using more sophisticated means like ransomware and spear-phishing," the report said.
The facts figure in a report submitted by Surinder S Rathi, additional district judge and OSD to Delhi Legal Service Authority (DLSA), before the court in pursuance of a direction that a comprehensive study be conducted on various issues including the cost incurred in running the criminal justice system.
The bench of justices Gita Mittal and J R Midha, which is yet to pronounce the quantum of sentence to three convicts including Vikas Yadav in the 2002 Nitish Katara murder case, had also asked DLSA to compute the cost incurred in the trial of this case, besides determining the compensation paying capacity of the convicts.
However, the reports gives no further details of cybercrime stalking the country.
Dealing with other crimes in the chapter, of 'Cost of Criminal Justice System', the report, quoting from the National Crime Records Bureau data, said that in 2013, as many as 66.40 lakh criminal complaints were received by the police stations across the nation.
It said that in Delhi alone, a total of 86,800 criminal complaints were received at its 175 odd police stations apart from around 89 lakh distress calls received by it last year.
"Although better part of the world has awaken to the exorbitant financial cost of running the criminal justice system, but our country is yet to take its first step in the right direction. Owing to mindless and unscientific planning all the wings of criminal justice system are highly chaotic in their functioning and are immensely overburdened," it said.
The report said that despite India having 12,700 odd police stations and 15.70 lakh policemen manning them, incidents of crime are spiralling uncontrollably.
"A lot is being done in this regard by all the stakeholders but unfortunately owing to lack of scientific methodology and concerted efforts of all concern not much headway could be achieved," the report said.
The report also said police, the first ring of criminal justice system, is in an almost pitiable state nationwide.
"Neither it (police) has the requisite manpower to deliver nor the technical expertise nor the infrastructure to contain crimes. To make things worse malice of corruption is eating into its vitals," the report said.
It said the judiciary, the second ring of criminal justice system, is also not "far behind in fulfilling its constitutional obligations and meeting the expectations of its citizen of delivery of timely justice".
"Courts are inundated with lakhs of case pending trial. Such is the snail pace of trials that influx of cases at any point of time is out doing the disposal. All this is resulting in piling up of cases in courts," the report said.
The report also added that the ancillary support system like jails, juvenile, justice boards, child welfare committees and forensic labs all need to be brought out of slumber and urgently to save this system from crumbling.
On the cost of criminal justice system, the report said that measuring the cost of criminal justice is not easy yet it is essential to the proper appraisal of any criminal justice system policy.
"There is an urgent need to develop a comprehensive methodology for calculating the cost incurred by society on account of various criminal offences," it said.
The report added that as on today, in India no empirical study has been conducted as to how much does a criminal case cost to the exchequer at the tax payers right from registration of the FIR to its logical conclusion post the trial in sentencing.
2017>2019: Data breach cost rises by 8%
From: Dec 14, 2019 Times of India
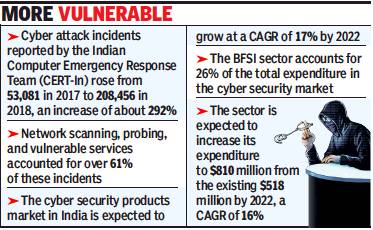
The average cost of a data breach in India has gone up to Rs 11.9 crore, an increase of 8% from 2017, a joint study by PwC India and Data Security Council of India (DSCI) said. As newer technologies shape the way people and organisations stay connected leaving a trail of data in the open, cyber security breaches have become commonplace.
With cyberattacks becoming more sophisticated, the average cost of a malicious insider attack rose by 15% in 2019 from last year. “Cyberattacks have evolved and increased in volume over the years. Attacks have become sophisticated in nature and types of attacks such as APT (advanced persistent threat), Zero Day, malwares, multi-vector attacks have become common, targeting core infrastructure such as ATM switches, payment interfaces,” Siddharth Vishwanath, leader of cyber security at PwC India, said in the report.
The cyber security market in India is expected to grow from $2 billion in 2019 to $3 billion by 2022, a CAGR of 15.6% — almost one-and-ahalf times the global rate, the report said. The study estimates that the cyber security market in India will be defined by three key sectors — banking & financial services industry (BFSI), IT & ITeS, and the government.
The BFSI sector, the report said, accounts for 26% of the total expenditure in the cyber security market. The sector is expected to increase its expenditure to $810 million from the existing $518 million by 2022, a CAGR of 16.1%.
Innovation in payments technology using AI, blockchain, IoT and real-time payments, and rising adoption of mobile point-of-sale (POS) devices have also contributed to the growth of potential security risks. Digital payments in India are expected to increase from $65 billion in 2019 to $135 billion in 2023, a CAGR of 20%. The report said that in order to maximise returns from cyberattacks, hackers are increasingly targeting core banking systems.
Country of origin
Chinese hackers
2016- 19: India 6th most targeted
Zuola had never fallen in with the party line. He would post translated news about Tibet, assert Taiwan’s sovereignty and call out misuse of government power. In 2010, on December 22, the Hunan-based cyber activist received a mail from a head-hunter offering a 400,000-yuan job (Rs 43 lakh) a year. It was too much money. Hours later, he got another mail from the ‘Taiwan Foundation for Democracy’ inviting him to a leadership camp. It was strange that the mail made it through the Great Firewall. Both were loaded with Trojans.
“The cyber army exists but within China there are not many reports. The cyber army has three kinds of targets — activists they need to shut down, overseas business companies for their IP (intellectual property) and governments for expanding influence,” Zuola told TOI. “Because I wrote about the government, I would get these APT emails.” APT, or advanced persistent threat, is a targeted, sophisticated and prolonged cyberattack. The kind that Indian intelligence agencies have been warning the country could be facing from China-based actors.
Since 2016, India has been the sixth most targeted country by China-based hackers — right after the US, South Korea, Hong Kong, Germany and Japan. Government sites came under attack most frequently, followed by telecommunications, media, high tech and transportation, according to a report shared with TOI by US-based cybersecurity firm FireEye.
In 2013, FireEye, then Mandiant, had established the presence of China’s PLA unit 61398, a “cyber espionage” unit of the Chinese military. Three victims of APT1, as it was called, were from India.IT, aerospace and public administration were most targeted. But a change was under way. The report says the Strategic Support Force set up in 2015 subsumed unit 61398 and other tech and space units under a streamlined Chinese Military Commission. The focus shifted to media sites. The agency “anticipates more aggressive efforts to influence public opinion in the future.”
Indian agencies have come under attack several times. A cyber espionage network of “the underground hacking community in China” compromising government systems in India was reported in 2010 by the Citizen Lab.
Cambodia, Myanmar. Laos
2024 Jan- April
Bharti Jain, May 24, 2024: The Times of India
New Delhi : Jamtara and Mewat have been upstaged as hotspots of financial cyber fraud in India, with 46% of defrauded money now bring lost to cybercrimes originating in southeast Asian countries such as Cambodia, Myanmar and Laos.
Organised cybercrime gangs, according to Indian Cyber Crime Coordination Centre (I4C) CEO Rajesh Kumar, are operating “corporate style” from hubs in these countries, hiring Indian jobseekers through illegal recruitment agents and then compelling them to defraud fellow citizens in India.
I4C and state law enforcement agencies have cracked down on some of these illegal recruitment agents. The foreign ministry has so far facili- tated the return of 360 Indians trapped in these cybercrime units, with 60 more due to return from Cambodia soon.
According to Kumar, Rs 1,420 crore was lost to 62,587 investment scams, Rs 222 crore to 20,043 trading scams, Rs 120 crore to 4,600 digital arrest scams and Rs 13 crore to 1,725 romance/dating scams, all originating from southeast Asia between Jan and April this year. Last year, more than one lakh investment scams originating from the region were reported on Indian national cybercrime reporting portal and 10,000 FIRs registered.
Large number of Chinese known to work in cybercrime hubs: I4C chief
Debit-Freeze On 3.2L Mule A/Cs In Last 4 Mths, 5.3L SIM Cards Suspended
Not ruling out China’s involvement in these scams, the Indian Cyber Crime Coordination Centre (I4C) chief said that a large number of Chinese people were known to work in these scam hubs and many of the suspected apps used for to defraud people are in Chinese language. Amid an overall increase in big ticket frauds reported in 2024, with over six lakh complaints involving a total amount of Rs 7,061 crore received on the national cybercrime reporting portal, I4C has intervened to save Rs 812.7 crore from being defrauded.
Collaboration between I4C and law enforcement agencies has helped debit-freeze 3.2 lakh mule accounts in last four months, get more than 3,000 URLs and 595 apps blocked under Information Technology Act, 5.3 lakh SIM cards and over 80,000 IMEI numbers suspended since July 2023. Also, there have been 3,401 cases of unlawful content being taken down from social media, websites and WhatsApp in last two months.
Indians who are lured to southeast Asia’s organised cybercrime factories with fake jobs advertised by illegal recruiters — detected in states like Andhra Pradesh, Tamil Nadu, Odisha and Delhi — are pushed into defrauding unsuspecting victims in India through social media advertisements and messaging promising quick financial gains on their investments or through gaming, digital arrests where the cyber offenders pose as as a law enforcement personnel; or romance, dating scams. “These gangs work in an organised manner, from scam compounds... many of them were linked to casinos earlier,” said Kumar.
The illicit gains from these cybercrime activities originat- ing in southeast Asia are laundered through sophisticated financial channels including Indian bank accounts, cryptocurrency transactions, cash withdrawals, etc, he added.
In May this year, Visakhapatnam cybercrime police had arrested three illegal recruitment agents who were sending gullible youth to Cambodia.
Similar arrests were carried out in Odisha. Ministry of external affairs has been working with Phnom Penh to rescue the Indians trapped in these compounds and get them home. Govt had earlier this month set up an inter-ministerial committee comprising various law enforcement and intelligence agencies to tackle the “spurt” in transnational organised cyber crimes being launched against Indians from southeast Asian countries.
TIMESVIEW: Cyber criminals are innovative. They regularly come up with new methods to dupe the susceptible. The sharp rise in such foreign-based operations is further cause for concern. Cybercops must raise their game to catch such offenders. This is also a note of caution for all. A few basic rules of online behaviour must be followed. Be fully aware and awake when dealing with money on the phone and online. Think carefully before making payment decisions online. Avoid clicking on fishy links. Eschew easy passwords. Don’t share an OTP number with someone you barely know. Staying vigilant is the only way to stay safe.
Cybercrime police stations
2019: Bangalore’s station exceeds limit, shuts
Kiran Parashar, Dec 4, 2019 Times of India
Call it a Y2K problem, magnified 5x. Bengaluru’s lone cybercrime station, which registers a large number of cases, has become a victim of its own record. Faced with the prospect of registering its 10,000th complaint this year, the station has shut down. Reason: The system’s inability to register a five-digit case.
This is the first time a police station in Karnataka has stopped receiving complaints because of such an issue. According to police sources, the station, located in the Bengalury City police commissionerate campus, received complaints till November 23. In all, 9,970 cases were registered at the station this year. Having registered an average of 30 cases a day, the station feared hitting the 10,000 mark on November 24.
A note announcing that the station is shutting down due to technical issues is pasted on its doors. The note also says complaints can be filed at any local police station or on www.cybercrime-.gov.in portal.
A senior police officer said the station personnel were working on and investigating the complaints already registered. DCP (crime-1) Kuldeep Kumar Jain said, “Since the portal used to generate FIR doesn’t take fivedigit numbers, we have stopped taking complaints in the cybercrime police station. This also means any police station in the state can register FIR till 9999 but not beyond that. The cybercrime police station of Karnataka is the only police station which has registered a huge number of cases.”
The city police seem to be in no hurry to fix the problem that might keep recurring. Ironically, the city police had recently conducted a hackathon to come up with technical solutions to crack crime. “We will resume registration of complaints from January 1,” Kuldeep said.
Cybersquatting
2000-20; Covid misinformation
Rupali Mukherjee, March 1, 2021: The Times of India
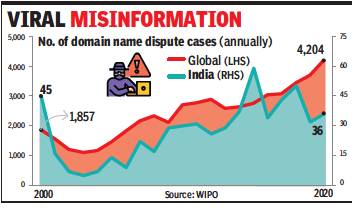
From: Rupali Mukherjee, March 1, 2021: The Times of India
A vaccine for Covid is out now. But sadly, there seems to be no cure yet for the misinformation being spread around the disease. And the ‘infodemic’ of coronavirus misinformation, which is rampant on social media, seems to be finding new avenues to spread.
Registration of domain names (representing corporate identity/brand on the internet) have been witnessing a surge, and are increasingly being used to spread misinformation, and engage in illegal and fraudulent activities. Strangely so, the surge in Covid cases seems to have fuelled the trend, with a spike witnessed in cybersquatting cases.
Cybersquatters are using terms like Covid-19, corona, drugs and vaccine within the disputed domain name for spreading widespread rumours, false information and misinformed campaigns, a World Intellectual Property Organization (WIPO) official told TOI. Simply put, cybersquatting is the abusive registration of trademarks as domain names, where an individual or company attempts to usurp online the reputation of an established brand.
In 2020, WIPO handled 4,204 cybersquatting cases — a nearly 14% increase over 2019. Examples include gilead-covid-19.com, plaquenilcanada24.com, dettolclean.com, cloroxvpn-.com, dishoom.delivery, sanoficovid19vaccine.com, business-facebook-covid-19.com, plaquenil400.com, brusselsmsf.org, sanofivaccincovid19.fr, allianzbills.com, belfius-quarantaine.com, clorox.life, and hmrc-refund-covid19.com. WIPO Arbitration and Mediation Center director Erik Wilbers said, “Among the many manifestations of cybersquatting is the abusive registration of internet domain names designed to capitalise on public health crises. Like earlier outbreaks such as bird flu and swine flu, the current Covid crisis attracts numerous infringing domain names registered to attract web traffic by combining pandemic-related terms with well-known trademarks.”
Recent cases where India is in the domain name include ford-india.com, gilead-india.com, volvoindiabus.com, amgenindia.com, montblancindia.com, sanofyindia.com, dettolindia-.com, and indiabetway.com.
Experts believe there is a surge in recent times due to a significant increase of digital technologies, and consequently an increased need of internet domain names. Covid has triggered the trend, since most people are working from home.
“Working from home has increased the business of ecommerce websites, given that most people have begun shopping from home as well, getting all required information/support at the click of a button. In the present scenario, given the effects of the pandemic, the most prone are social media and pharma sectors. With widespread rumours, false information, misinformed campaigns, encouraging use of non-prescribed drugs, etc, being channelised through domains similar to popular websites such as Google (coronavirusgoogle.com), Facebook (facebookcovid19.com) have caused a significant impact. While these companies have managed to tackle these issues by opting for the Uniform Domain-Name Dispute-Resolution Policy, it is likely that similar issues will continue to occur and it is important that companies are always proactive in their approach to protect their brands and related domain names,” J Sagar Associates partner Tony Verghese said.
In India, there are no specific laws on cybersquatting. The principal safeguard for companies is ensuring the appropriate registration of their trademark/s.
KPMG India partner & head (cyber security) Atul Gupta said, “Organisations spend significant time, resources and energy on establishing trust, which includes brand, reputation and goodwill (that is, digital trust on web channels) and need to be extremely considerate of domain names (including lookalikes on the internet) to ensure that there is no impact on the digital trust. Cybersquatters are also using similar domain names to inflict significant damage, also called ‘typosquatting’, which includes making a small change in the original domain name and normally not easy to detect. ”
Regular monitoring and enforcement of any infringements, defensive measures such as blocking services, and issuing cease-and-desist notices proactively are some of the other safeguards that could be adopted by companies, Verghese added.
Cyber insurance
India’s rank in the world: 2023

From: Sep 4, 2024: The Times of India
See graphic:
Cyber insurance in India vis-à-vis Australia, France, Germany, Japan, Singapore, the UK and the USA: presumably as in 2023
Data-breaches
2016, 2017: Major data breaches
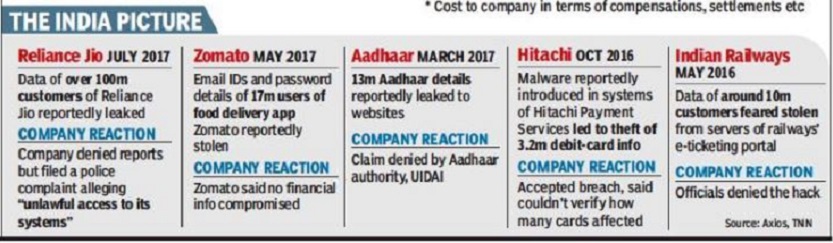
From The Times of India Friday, 01 December 2017
See graphic, ' Major data breaches in India, 2016 and 2017, the number of persons affected '
2016-17: 9 large data leaks that affected India
March 31, 2018: The Times of India

From: March 31, 2018: The Times of India
All data leaks are not equally harmful and a leak is generally less harmful than a data breach. Here are some of the large leaks that made headlines
Hacking of websites
Government websites/ 2013- 16
Over 700 govt websites hacked from 2013 to 2016, Feb 8, 2017: The Times of India
More than 700 websites of central ministriesdepartments and of state governments were hacked between 2013 and 2016, Lok Sabha was told.
As per information reported to and tracked by the Computer Emergency Response Team (CERT-IN), which works under the IT ministry , as many as 199 websites of central ministriesdepartments and state governments were hacked in 2016, compared to 164 in 2015, 155 in 2014 and 189 in 2013. This information was shared with Lok Sabha by minister of state for home Hansraj Gangaram Ahir in a written reply.
Of the 8,348 persons arrested under different provisions of law relating to cyber crime, only 315 were con victed during 2014-15, the government said.
In a recent cyber attack, the website of National Security Guard (NSG), a paramilitary force comprising anti-terror crack commandos, was partially defaced and abusive messages posted on the home page by unknown hackers on January 1.The website was blocked immediately .
Similar cyber attacks were also reported on websites of ordnance factories as well as railways. Ahir said the government had initiated several policy, legal and technical measures such as audit of the systems and networks, increasing awareness in area of cyber security , sharing threat-related information with stakeholders, issuing advisories on such threats through CERT-IN and National Critical Information Infrastructure Protection Centre (NCIIPC), and capacity development to address the issue of cyber hacking.
Ransom paid, country-wise
As in 2019-20
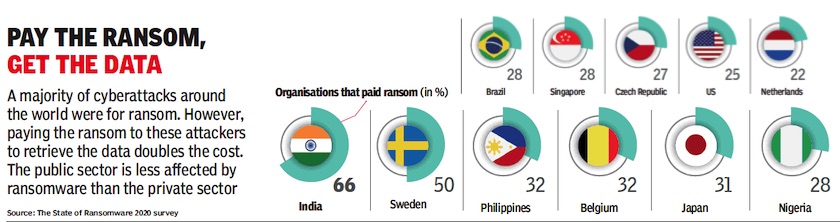
From: June 4, 2020: The Times of India
See graphic:
Ransom paid to cyber attackers, country-wise, as in 2019-20.
Spamming
2020: Two spammers make India no. 7
Chandrima Banerjee, July 29, 2020: The Times of India
India sent out 7.8 billion spam emails in the past 24 hours, making it the world’ seventh biggest spammer, up three places since the beginning of the month. And it has been pushed largely by two users — one in Mumbai and another in Ghaziabad — realtime email and spam data by Cisco’s cybersecurity wing Talos Intelligence show. Over the past month, the volume of spam from India has grown 45% while the volume of email went down 20%.
The Mumbai-based user is the second biggest spammer in the world as of Tuesday, right behind two users in emerging cybercrime hub Vietnam, and started operating at the end of last month. “The IP has only recently started sending mails,” internet security technology company Cyren’s IP check said, flagging it. Four places behind it in the global spam rankings is another Indian user, from Ghaziabad, who had no email activity till July 22. In five days, its email volume went up 2000% over the previous month’s average. The IP’s email reputation is poor, “a problematic level of threat activity… email traffic is likely to be filtered or blocked”, according to Talos.
“A jump in email activity alone can mean a number of things. For example, it could be a new legitimate service, it could be someone who has a machine that has been compromised, but it could also be someone sending malicious messages, intentionally, for profit,” Craig Williams, director of outreach for Cisco Talos, told TOI.
In terms of email volume, no Indian IP address figures in the top 100. But when it comes to spam, the two Indian IP addresses are among the top 10 in the world. They have, in fact, been flagged by other cybersecurity agencies as well for snowshoe spam — in which spam is spread out over several domains and IP addresses to avoid detection — which would mean the actual volume of malicious mails sent out is much higher.
For June last year, the share of spam in global email traffic was under half, 46%. Now, riding the coronavirusthemed attack wave, it is 85%. Malware generation from the country has also been high. Six IP addresses in India made India the world’s fourth biggest malware sender. All of them are on the same network in Bengaluru.
Technology scams
2018, 2021
Manash Gohain, July 23, 2021: The Times of India
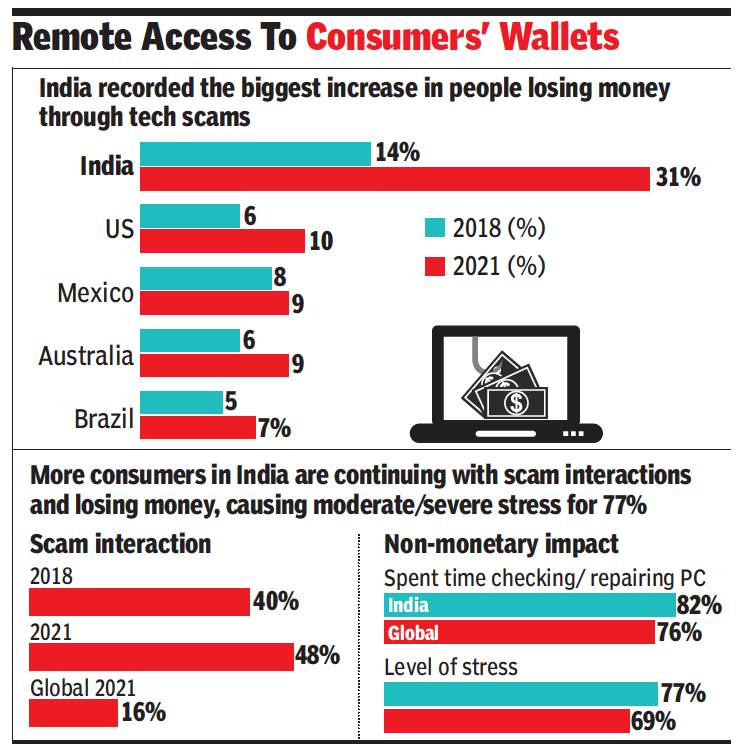
From: Manash Gohain, July 23, 2021: The Times of India
India is a hub of call-centre talent put to criminal use, says Microsoft’s new research report. Its survey of 16,254 adult internet users in 16 nations found that nearly seven out of 10 consumers in India were targeted by a tech-support scammer in the past one year.
The ‘Global Tech Support Scam Research’ showed that India experienced a relatively high scam encounter rate of 69% in 2021, almost similar (70%) to that in 2018. In contrast, there was an overall five-point drop in scam encounters globally with a rate of 59% over the same period.
In India, one in three (31%) of those surveyed continued engaging and eventually lost money, an increase of 17 points as compared with 2018. Millennials (aged 24-37) were the most susceptible, with 58% of those that continued with a scam incurring monetary loss. As much as 73% of men in India who proceeded to interact with a scammer were likely to lose money, the survey said.
Every month, Microsoft receives around 6,500 complaints globally from people who have been the victims of tech-support scams. This is down from 13,000 reports in an average month in prior years.
Posing as executives of a tech major, such as Microsoft or Google, the scammers contact users and create a fear psychosis or convince them to install a software. Once done, it gives the fraudsters illegal ‘remote access’ to their victim’s devices. The scammers then drain the victim’s money.
2015: Rise in complexities of hacking
Rajshekhar Jha, The Times of India, Dec 27, 2016
Most Investigators Have Little Knowledge About Complexities Of Hacking
When high-profile websites are hacked into, they make news. But there are hundreds of such acts that escape public attention, leaving in their wake financial and social ruin. But Delhi Police, while registering cases for computer-related offences and for online posting of sexually offensive content, often finds itself hard-pressed to prove these crimes in court.
In 2015, Delhi Police registered 77 FIRs under the Information Technology Act, but could make arrests and file charge sheets in only half the cases. Of the 16 cases filed for publishing of sexually offensive content, charge sheets were filed in just four cases and three arrests were made.In 2014, the record was poorer.That year, the police could not file a single charge sheet in the cases on posting of sexually offensive content.
In the meantime, cybercrime is on the rise. In December last year, a south Delhi firm lost several crores of rupees when hackers routed the money from one of its London clients to accounts in Turkey .Hackers had used the firm's email ID to request the client to change the beneficiary account s. A few months later in February , crooks -later tracked to a north-east India state -hacked the account of a city businessman and made off with Rs 13.5 lakh in two transactions. Then in September this year, the CEO of an asset management company had his ID hacked and several lakhs transferred from the company's account into the hacker’s.
If your bank account has been targeted by cyber crooks, chances are bleak that you'll get your money back, Delhi Police's record in handling such cases indicates.Sources say recovery of “stolen money“ in cyber-crime cases is rare even if the accused is nabbed. The time taken to solve such cases is a major contributing factor in the loss of the money .
“Mostly , the money is spent in the initial days itself whereas we are able to get IP logs after a week, even in highpriority cases. The money is transferred to multiple accounts and withdrawn from ATMs as well,“ said an officer.
The poor record of Delhi Police on online crime is perhaps due to the cyber cells being manned by cops who have little knowledge about the complexities of hacking. A sub-inspector in one of these cells, on being promised ano nymity , told TOI that he barely knew how to use a laptop.“Hum toh raid pey jaate hain, dhar-pakad karte hain. Computer wala kaam to oopar se hota hai, private log karte hain (We only conduct raids and make arrests. Private individuals deal with technical issues),“ he admitted.
The “private individuals“ he referred to are apparently ethical hackers. “They help us in tracking internet protocol addresses and on other technical issues,“ explained a senior officer. Obtaining the IP addresses of the offenders quickly is one of the toughest hurdles for the cops, said a senior officer of a cyber cell, because they use multiple addresses or operate via dark webs . “By the time the details arrive, it's too late,“ he said.“In cases where money has been siphoned off, delays render the case almost unsolvable.“ The outsiders also help police deal with techniques like IP masking that hackers resort to in order to hide their identity .
PART II
YEAR-WISE STATISTICS: CYBER-CRIMES
CYBER-ATTACKS
2013-14
Feb 17 2015
Cyber mobbing
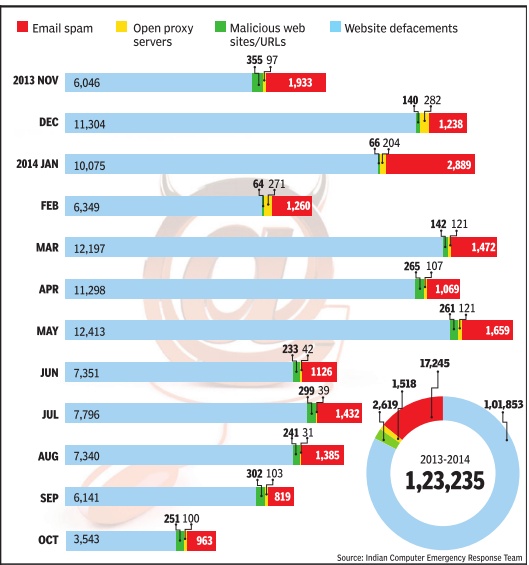
Indian Computer Emergency Response Team (CERT-In) is the national incident response centre for major computer security incidents. It works under the department of electronics and information technology and its primary role is to raise security awareness as well as provide technical assistance for recovering from cyber attacks. CERT-In's monthly incident data suggests that between November 2013 and Oct 2014, on an average there were about 12,000 cyber attacks. The highest number involved email spam identical messages sent to numerous recipients by email that may include malware as scripts executable file attachments or hyperlinks. It was followed by website defacements and open proxy servers--servers that operate by concealing IP address and are used to circulate pornography.Malicious websites that redirect users to sites that download malicious code to their computers were also identified as a threat.
2013- June 2021
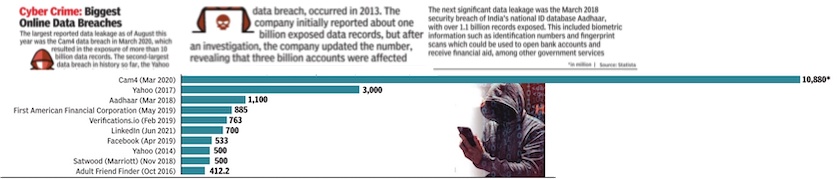
From: Sep 5, 2022: The Times of India
See graphic:
Cyber crime, 2013- June 2021
CYBER-CRIMES, Overall
2001-13
The Times of India Sep 01 2014
The Information Technology Act, 2000, identifies certain practices like hacking, publication and transmission of obscene material, breach of privacy and so on as criminal. Forgery, criminal breach of trust etc. done with the help of information technology are also officially recorded as cyber crime.In 2001, the country's first cyber crime police station was opened in Bangalore and in the 12 years to 2013, just 18 more special purpose police stations were added. Meanwhile, there has been a multi-fold increase in such crimes accompanying a massive increase in internet subscribers.

2006-15: Cyber crime, an increase
The Times of India, Sep 01 2016
Vishwa Mohan
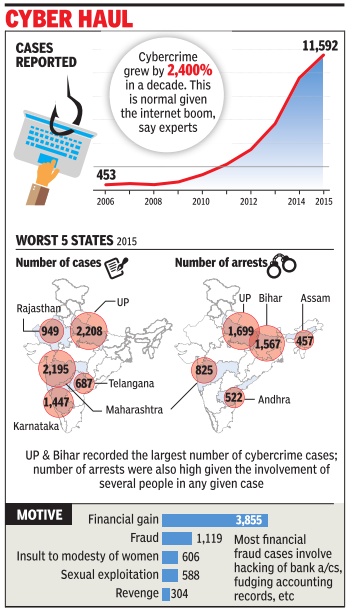
With the internet and social media becoming a way of life, cybercrime numbers have steadily climbed over the years. Such crimes went up 20% in 2015 compared to 2014, logging a 2,400% increase over the decade 2005-15.
The National Crime Records Bureau (NCRB) report shows that cybercrime cases rose from 9,622 in 2014 to 11,592 in 2015, nearly onethird of the crimes committed for financial gain.
The number of people arrested in cybercrime cases rose by over 41% during the same period -from 5,752 in 2014 to 8,121 in 2015.
Besides crimes for financial gain, the motives also included cheating, insulting women, sexual exploitation and personal revenge or settling scores.
The report cited `political motives', which could be related to tarnishing the image of opponents through morphed pictures or fudged data. The report said 44 cybercrimes cases for `political motives' were reported in 2015.
Data theft, breach of an individual's internet banking or other service platforms through hacking, cyber stalking, digital forgery such as fabrication or destruction of electronic records were some methods used by criminals in the internet space.
An analysis of past NCRB reports revealed that the number of cybercrimes was quite low 10 years ago, with only 453 such cases reported in the country in 2006. Barring 2008 when the number of cases fell compared to 2007, the numbers have consistently risen.
Though the NCRB did not give any reason for the rising figures, they could be attributed to increasing internet penetration in the past few years. Use of internet for various services has led many to use the web for multiple purposes -be it personal and official communication, banking, teaching, e-marketing, digital lockers or social networking.
The latest NCRB report said Uttar Pradesh, Maharashtra, Karnataka, Rajasthan and Telangana reported the highest number of cybercrimes last year. All five states are home to several companies dealing with information technology and related services.
In terms of arrests, Bihar, Andhra Pradesh and Assam made it to the list of top five.Experts said this could be attributed to multiple people's involvement in one case.
Uttar Pradesh recorded the largest number of cybercrime cases largely because of its spread and resultant internet penetration in major cities and in the hinterland as well. The state's figures could also be high due to the IT destination of Noida which has emerged as a hub of cyberattacks in the country .
2011-14: Online frauds
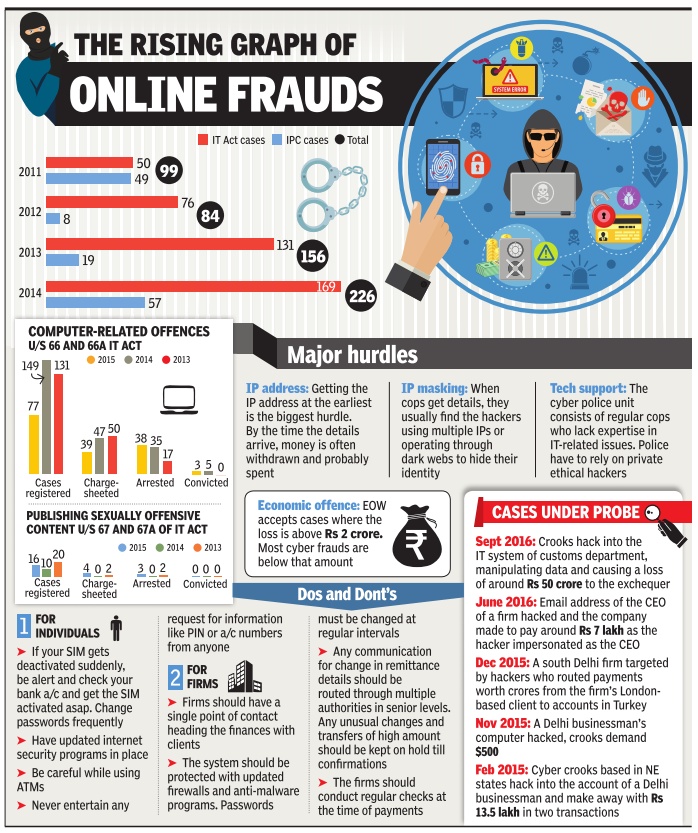
See graphic, 'Online frauds, 2011-14 and computer-related offences under Section 66 and 66A IT Act, 2013-15'
2012
The NCR, Bangalore. Vishakhapatnam
Cyber crime cases up by 46%
Dwaipayan Ghosh TNN
New Delhi: Delhi is far from being the IT capital of the country. But over the last few years, there has been a concentration of IT companies in the NCR [National Capital Region]. And there has been a sharp rise in cases of cyber crime. Data released by NCRB [National Crime Records Bureau] say it all—there has been a 46% rise in the number of cases under the IT Act in Delhi, while in Faridabad and Ghaziabad the increase has been 67%.
Delhi Police registered 73 cases under the IT Act in 2012 and arrested 17 people, including a foreign national. This was significantly higher than the figures for 2011 when 50 such cases were registered under the said Act. However, the total number of cases registered came down to 80 from 99 in 2011, as cases registered under common IPC sections dropped to just seven in 2012 from 49 in 2011.
However, the NCR figures are far less as compared to Bangalore (342 cases) and Vishakhapatnam (153).
Those involved in such crimes in Delhi were found to be between 18 and 45 years of age. Most of the criminals were stalkers but some also did it for extortion or out of business rivalry.
Earlier this year, Delhi Police's cyber crime cell had launched an awareness campaign aimed at curbing rampantincreasein cyber crimes, especially among minors. As part of it, police asked children to refrain from entering adult and hate sites and educated them and their teachers about the cyber laws of the country.
Police said that 245 cases involving creation of fake profiles and 51 defamation lawsuits were filed last year. Most of the victims were minors. Police have been considering to appoint ‘internet safety officers’ in Delhi schools by training designated teachers. S D Mishra, additional deputy commissioner of police in the Economic Offences Wing, said that parents will also be brought on board for proper guidance.
Mumbai
Mumbai sees 218% spike in cyber crime
V Narayan & Sumitra Deb Roy | TNN 2013/06/15
Mumbai: The city saw a 218% rise in cyber crime cases in 2012, with 33 cases registered under the Information Technology (IT) Act and 72 under the Indian Penal Code (IPC), according to the National Crime Records Bureau. The total of 105 cases was way over the 33 total cases registered in 2011. In fact, the 2011 figure was a 32.7% drop from the previous year’s 49 cases. Nationwide, Mumbai saw the third highest number of cases registered under the IT Act in 2012, with Bangalore and Pune topping the list.
State-wise, Maharashtra recorded more cyber crime than any other state, with 471 different offences registered under the IT Act and 90 under the IPC in 2012. The total of 561 cases was a 42.7% increase from the 393 cases registered the previous year. Andhra Pradesh was second with 454 cases and Karnataka third with 437 cases registered under both categories in 2012.
2013
Bangalore
Cybercrime: 509 cases in Bangalore, no conviction yetbb
The Times of India Rajiv Kalkod,TNN | Jun 29, 2014
Cybercrime: 509 cases in Bangalore, no conviction yet
Thirteen years, 509 cases and 144 charge sheets. But not a single conviction. That's the track record of the cybercrime cell of the state's criminal investigation department (CID).
BANGALORE: Thirteen years, 509 cases and 144 charge sheets. But not a single conviction. That's the track record of the cybercrime cell of the state's criminal investigation department (CID).
With the CID filing a chargesheet in against ADGP P Ravindranath for allegedly taking objectionable photos of a woman at a coffee joint, the pertinent question that arises is: Will Ravindranath break the record of the cybercrime cell and be convicted?
Documents with STOI reveal that since its inception in 2001, the cybercrime cell has investigated 509 cases and filed chargesheets in 144 of them - none of them ending in conviction. Of the 509, 181 cases were closed under 'C reported' (No evidence found) category while 85 have been B reported (Faulty complaint).
Reacting on the zero conviction, a senior police officer told STOI that the charge sheet weakens when court asks for the accused's presence at the time of offence. "In many hacking and phishing cases, we establish the source; that is the accused's computer. But whether the accused was there at the time of offence, is a little hard to establish and this helps the accused in walking out free," he said.
Delhi
72% rise in cyber crimes, cops run into tech hurdles
Raj Shekhar New Delhi:
TNN
The Times of India Jul 02 2014
Cyber crimes registered under IT Act in 2013 shot up by 72.4%--131--compared to 2012, when only 76 cases were reported. The offences under IPC (forgery/ cheating) have increased by 137.5%--19 cases were filed in 2013 in contrast to eight in 2012, according to the data released by National Crime Records Bureau. NCRB ranks Delhi 12th in the country.
The maximum cases-99--are related to hacking, which has been divided into two sections. Under the first section--loss and damage to computer resource and utility--60 cases have been filed. The remaining 39 cases come under “hacking for other purposes“.
The offence categorized as obscene publication/transmission in electronic form has 20 cases under it.
Two cases of fake digital signatures were registered for the first time in 2013, while 10 cases involved breach of privacy. Most cyber offences had harassment, teasing and fraud as the motive. There were nine cases where the intention was to cause disrepute, while two cyber crimes were categorized as a prank. NCRB hasn't elaborated on the motive behind 90 cases, which have been put under the “others“ section.
A majority of the suspects are neighbours and students.
Of 150 suspects, 23 were students and 20 were neighbours.
Disgruntled employees and employers were suspects in seven cases, while six were business competitors. Surprisingly, only two foreigners were suspects, according to the NCRB data. The category of 92 suspects hasn't been mentioned.
Police, however, could arrest only 38 people in cases under IT Act, pointing to a poverty of infrastructure and investigation skills. Twenty of the offenders were in the age group of 18-30, while 15 were between 30 and 45. Only three people in the age-group of 4560 were arrested under the act, which broadly includes offences committed through electronic means. Only seven people were arrested for cyber offences registered under IPC.
Cops says inadequate infrastructure and correspondence with the World Wide Web authorities slow them down.
“Most of the investigation revolves around tracing IP addresses and the servers used to commit the crime. It takes a lot of time to get these details,“ says a cyber cell officer.
Delhi Police has been trying to stay up to speed. Its cyber crime cell had also launched an awareness and safety campaign to curb the menace.
Asking children to refrain from entering adult and hate sites, informing them of cyber laws, creating awareness among school administration and teachers were highlights of the programme.
The unit had also planned to procure a cyber forensic van to pick up electronic evidence from the scene of crime so that it can be analysed instantly .
Mumbai: 168% increase
Cybercrime rises 168% in just one year
The Times of India V Narayan | May 14, 2014
Cybercrime has seen an alarming 168% rise in just a year. From 63 in 2012, the number of cases went up to 169 in 2013, as per Mumbai Police.
This year, the number of cases was 54 in just the first quarter; by the year-end, it is expected to cross the 200 mark—almost half of the 421 cybercrime cases recorded in Mumbai from 2010. Also, experts say, more money will be lost to cybercrime this year than in the last three years put together.
Sending obscene emails, SMSes and MMSes tops the chart, with 84 cases registered in the city from 2010, followed by credit card fraud (78 cases).
The police say card fraud is the most worrisome trend. From 2012 to 2013, it rose by 300% (8 to 32 cases). This year, seven cases were registered till March 31, almost equal to the number of cases in all of 2013. The incidence of sending obscene emails, etc, rose by over 191%—from 12 in 2012 to 35 in 2013.
As for hacking, 32 cases have been registered since 2010, with its incidence going up from two in 2012 to eight in 2013. Also, eight cases have been registered in the first quarter of this year—a sign of things to come.
Worldwide
Jan 12 2015
Diwakar
2013 saw 62% rise in no. of data breaches compared to 2012
The recent cyber attack on Sony Pictures by North Korean hackers has again put the spotlight on the dangers stalking a world digitally connected like never before. Till now mainly restricted to personal computers and laptops, the threat will only get bigger with smartphones and tablets becoming devices of daily use.
The mysterious attack on the Baku-Tblisi-Ceyhan pipeline, which was built with US encouragement and despite Russia’s reservations, is seen as marking the beginning of a new era of cyber war. It has been blamed on Russian cyber spies who were suspects also in the attack on JP Morgan Chase.
The Russian groups have become so emboldened that they targeted several German government websites on Wednesday, including the official page of Chancellor Angela Merkel.
The US security establishment itself now boasts of 6,000 cyber warriors — the crack troops who are suspected to be behind the crippling of North Korean internet networks following the Sony attack — and is prepared for a digital Peral Harbour.
Globally, security analysts called 2013 the year of the mega breach, with a 62% increase in the number of data breaches compared to 2012. The year also saw a 91% increase in targeted attacks. Both sophistication and brazenness of cybercrime syndicates or, for that matter, “hactivists” has increased.
‘Spearfishing’, which involves intelligent emails targeted at individuals, catching targets off guard by making “emotional connection” where criminals back up enticing emails with phone calls to win the victims’ trust, focusing on “watering holes” which are frequented by targets and throwing baits like “free” broadband connections show the expanded arsenal of cyber criminals.
Growing incidence of the use of ‘Cryptolocker’ virus and ‘ransom ware’ to force victims to buy decryption software or pay up to secure the release of his device and files signals the audacity of the gangs prowling cyber space, whose attacks on leading names in business like Target, Ebay, JP Morgan Chase, Adobe and Home Depot led to huge plunder of credit card and debit card details of their customers. Companies also suffered hugely on account of erosion of trust. Recently, Symantec, a software security major, uncovered a new piece of malware — Regin — which bears the hallmarks of a state-sponsored operation and is believed to have been in use since at least 2008.
It, just like ‘Dragonfly’, another malware which appears to be a state-sponsored effort, is persistent in seeking access to targets and stealing information and is far more complex than Stuxnet, which was used to target Iran’s nuclear plants. Experts at Symantec believe many components of Regin remain undiscovered and it may have more versions and can perform more functions for cyber espionage and sabotage.
Michael Counsel, chief technology officer and vicepresident consulting, products & services, Asia Pacific and Japan, said Symantec’s cyber threat intelligence had helped the firm identify some significant threats including Regin and other highly adept attack groups like the Dragonfly that was behind several sophisticated attacks on industrial control systems in the energy sector in the US and Europe.
Talking about the need to successfully defend against targeted attacks, Counsel said businesses needed to expand their focus from prevention to detection and response. While the threat of attack on individual targets by immobilizing their cars and medical devices doesn't seem distant anymore, cyber criminals can inflict immense harm on companies by reaching them through their vendors, a soft underbelly according to Symantec, to steal data and intellectual property .There is a gang, ATP Group, which specifically targets hotel guests, while also attacking “smart meters' to disrupt power supply in cities.
`Distributed denial of service' attacks in which servers are flooded with traffic until they collapse -have become a tougher challenge. Symantec, which was engaged by FBI and EuroPol Scotland Yard and other government agencies to take down `Blackshades', a powerful and popular Trojan, Zeus Botnet and Major Cryptolocker, concedes cyber crime networks have become more resilient and taking down new Botnet attacks will be difficult.
2014-16
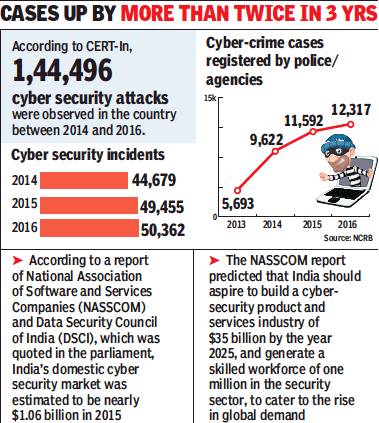
ii) cyber-crime cases registered by police-agencies, 2013-16
From: Neeraj Chauhan, January 18, 2018:The Times of India
See graphic:
i) Cyber security incidents, 2014-16;
ii) cyber-crime cases registered by police-agencies, 2013-16
2014-June 2017
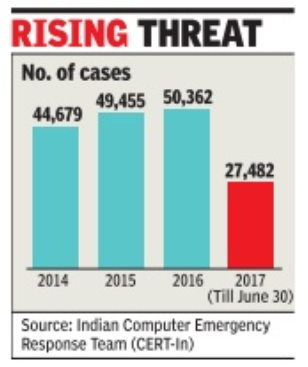
Chethan Kumar|One cyber crime in India every 10 mins|Jul 22 2017 : The Times of India (Delhi)
From the global ransomware attacks that hit hundreds of systems to phishing and scanning rackets, at least one cyber crime was reported every 10 minutes in India in the first six months of 2017. That's higher than a crime every 12 minutes in 2016.
According to the Indian Computer Emergency Response Team (CERT-In), 27,482 cases of cyber crime were reported from January to June.These include phishing, scanning or probing, site intrusions, defacements, virus or malicious code, ransomware and denial-of-service attacks. With more Indians going online, cyber experts said putting in place critical infrastructure to predict and prevent cyber crimes was crucial. India has seen a total of 1.71 lakh cyber crimes in the past three-and-a-half years and the number of crimes so far this year (27,482) indicate that the total number is likely to cross 50,000 by December, just as in 2016.
“It is not just enough to make efforts at the government level, which is, in some sense happening, but cyber crime affects hundreds of individual systems and firms, all of whom need to be ready with specialised teams,“ cyber crime expert Mirza Faizan Asad said.
While India has been dealing with crimes such as phishing and defacement, ransomware attacks have come as a surprise. Analysis of data from 2013 to 2016 shows that network scanning and probing -seen as the first step to detect vulnerabilities in systems so that sensitive data can be stolen -formed 6.7% of all cases while virus or malware accounted for 17.2%.
Experts pointed out that these were indications of increasing cyber crime-asa-service (CAAS), besides attempts at ransomware.“There has to be a concerted effort to treat cyber security seriously ... The vast majority of organisations are looking at cyber security as a compliance task and thus do the minimum possible to achieve that,“ Asad said.
Increasing ransomware threat and the demand for ransom in bitcoins -a crypto-currency which attackers feel is the safest way to get paid -saw the SC direct the RBI to take cognisance of the matter. The RBI has also been issuing regular warnings on bitcoins.
2017
July 7, 2018: The Times of India

From: July 7, 2018: The Times of India
Cyber crime cases across India rose 44% between 2013 and 2017. Of the 3,474 cyber crime cases reported in India last year, a majority related to online banking — indicating the need for stronger digital policy even as the government makes a push for going cashless.
Bengaluru top city for cybercrime cases
Oct 23, 2019: The Times of India
When it comes to registering cybercrime-related cases, Bengaluru tops the list among metropolitan cities in the country.
And, of the 21,796 cyber crime cases registered in the country in 2017, identity theft accounted for the highest number (3,724), followed by fraud (3,466), cheating (1,896) and publishing/transmission of obscene or sexual explicit material in electronic form (1,768).
For the first time, NCRB compiled data on cyber crimes relating to fake news on social media with as many as 179 such cases registered across the country in 2017.
According to the latest data, some 2,743 cybercrime cases were registered in Bengaluru in 2017. In other words, Bengaluru accounted for 38% of all cybercrime cases reported in the country. Mumbai and Jaipur come next with 1,362 cases and 685 cases, respectively. A senior police officer said, “Bengaluru police are more open to registering cybercrime complaints. Since the city is the country’s technology capital, the awareness level among the people is high and they would not step back from filing a complaint with police.”
Nationally, the total number of cyber crime offences reported in 2016 stood at 12,317 and in 2015, 11,592. The maximum cases registered in 2017 were in Uttar Pradesh (4,971, up from 2,639 in 2016), followed by Maharashtra (3,694 as compared to 2,380 in 2016) and Karnataka (3,174, up from 1,101 in 2016). TNN
2018
2018: Bengaluru vis-à-vis Delhi
January 10, 2020: The Times of India
NEW DELHI: The capital has witnessed more cybercrime incidents — 189 — in 2018 as compared to 162 in 2017. While most of the offences — 43 — were computer-related frauds, 32 involved sexual exploitation of women, 28 cyber stalking, 17 publishing sexually explicit content, nine other frauds and three bullying children on the net. In 35 cases, chargesheets have been filed.
In 2018, the cops also disposed of 460 cases, including the ones pending for the past two years.
According to National Crime Records Bureau (NCRB), the figure was just 2% of the 10,098 cybercrime cases reported in 19 major cities in 2018. Bengaluru was at the top with 5,253 (32.5%) incidents. While fraud was the motive in the majority of the cases, extortion, personal revenge and playing pranks were the other common reasons.
The cybercrime unit of Delhi Police registered 15 cases of identity theft, eight of cheating using a computer device and 34 of publication or transmission of obscene and sexually explicit act in electronic form. No case was lodged under the head of cyber terrorism. In 2018, the cops probed 163 cases of cybercrime, during which 77 people were arrested and 49 chargesheeted. Only two accused were convicted.
In 2017, Delhi Police had launched a dedicated website where the victims of cybercrime can lodge a complaint. A cyber laboratory to help in such cases was also set up.
2019
Cyber crimes soared 64% nationally in 2019, October 1, 2020: The Times of India
Cyber crimes registered a 63.5% rise in 2019, with overall cases increasing to 44,546 from 27,248 in 2018 and 21,796 in 2017 as per latest NCRB data. In the cities, a total 18,732 cyber crimes were registered, marking a whopping 81.9% rise over 2018. A profile of cyber crimes in 2019 shows that fraud was the motive in 26,891 cases (60.4%), sexual exploitation in 2,266 cases (5.1%), causing disrepute in 1,874 cases (4.2%), extortion in 1,842 cases, pranks in 1,385 cases, personal revenge in 1,207 cases; and anger in 581 cases.
2019, Q2
Sindhu Hariharan, August 13, 2019: The Times of India
India has emerged as the ‘most vulnerable’ to cyberattacks due to the deployment of Internet of Things (IoT) systems. On February 28 this year, the day of heightened tensions between India and Pakistan, the country found itself as the most-targeted nation as it experienced a large spurt in attacks, according to a recent study by cybersecurity firm Subex. The country also saw a 22% jump in total number of attacks in the IoT segment during the quarter ended June, the report said. Globally, cyberattacks increased by 13% during the same period.
The Bengaluru-based Subex captured details of attacks from its “honeypot” network (a decoy computer system for trapping hackers) that covers over 4,000 IoT devices. During the June quarter, Subex researchers recorded 33,450 high-grade attacks, 500 of which were of “very high sophistication”.
As many as 15,000 new samples of malware were discovered this quarter and, in a sign of increased sophistication of threats, 17% of the samples collected were modular malware — an advanced attack on a system that acts in different stages.
Subex MD and CEO Vinod Kumar said there are also strong geopolitical influences seen in some of the attacks on critical infrastructure with patterns of IP-spoofing with an intent to hide the geography of origin. Even as IoT in India moves from proof of concept to full-scale deployments rapidly, the country’s deep expertise and preparedness level hasn’t kept pace, he added. IoT systems related to smart cities, financial services, and transportation sectors were the top targets for hackers, accounting for over 51% of all cyberattacks registered.
2020
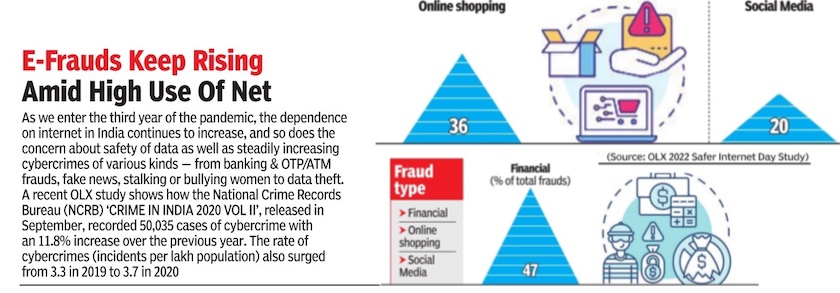
From: February 15, 2022: The Times of India
See graphic:
Cyber-crime in India in 2020
2022: In the metros

From: June 16, 2025: The Times of India
See graphic:
Cyber- crime, 2022: In the Indian metros