Chinese cyber-attacks on India
This is a collection of articles archived for the excellence of their content. |
Contents |
2012-18
Attacks on Indian satellite communications
Chethan Kumar, September 23, 2020: The Times of India

From: Chethan Kumar, September 23, 2020: The Times of India
Computer network attack against Indian satellite communications in 2017” is one among a slew of counter-space activities carried out by China since 2007, listed in a new report by US-based China Aerospace Studies Institute (CASI), which provides China’s space narrative among other things. Isro, while conceding that cyberattacks are a constant threat, maintains that its systems have not been compromised so far. The 142-page report notes that between 2012 and 2018, China carried out multiple cyberattacks, but elaborates on the result only in one case.
In 2012, a Chinese network-based computer attack on the Jet Propulsion Laboratory (JPL), the report points out, “allowed ‘full functional control’ over JPL networks”. The report quotes multiple sources while listing out some of these attacks.
India, as part of its counter-space capabilities, demonstrated Anti-Satellite (ASat) missile technology on March 27, 2019, which equipped India with a ‘kinetic kill’ option to destroy enemy satellites. But the CASI report points to how China has multiple other counter-space technologies that are intended to threaten adversary space systems from ground to geosynchronous orbit (GEO). These include direct-ascent kinetic-kill vehicles (anti-satellite missiles), co-orbital satellites, directed-energy weapons, jammers, and cyber capabilities.
CASI, a think-tank, supports the secretary, chief of staff of US air force, the US chief of space operations, and other senior air and space leaders. It provides expert research and analysis supporting decisions and policymakers across the US government. CASI supplements findings of a recent US Pentagon report which had said that PLA continues to acquire and develop technologies China could use to “blind and deafen the enemy”.
Isro, multiple insiders said, hasn’t been able to pinpoint sources of cyberattacks over the years. “Cyber threats are a given but it cannot be ascertained who are behind such attacks. We’ve systems in place to alert us and I don’t think we’ve ever been compromised,” a senior scientist said, adding that “the Chinese may have tried and failed”.
Isro chief K Sivan denied any direct knowledge of such an attack on Indian ground stations. “The threat perception is always there and it’s not unique to India. We’re secure,” he said. The scientist said India has an independent and isolated network that is not connected to the public domain, including the internet, which has kept its systems safe.
2021
Targeting Indian port
Chinese hackers are still actively targeting Indian port in shadow war, US firm says
NEW DELHI: At least one connection opened by Chinese state-sponsored hackers into the network system of an Indian port is still active, even as authorities block attempts to penetrate the nation’s electrical sector, according to the US firm that alerted officials.
As of Tuesday, Recorded Future could see a ‘handshake’ -- indicating an exchange of traffic -- between a China-linked group and an Indian maritime port, said Stuart Solomon, the firm’s chief operating officer. Recorded Future calls the group RedEcho and says it had targeted as many as 10 entities under India’s power grid as well as two maritime ports when the company first notified India’s Computer Emergency Response Team on February 10. Most of these connections were still operational as recently as February 28, Solomon said.
“There’s still an active connection between the attacker and the attackee,” Solomon said, referring to the port. “It’s still happening.”
A spokesman for India’s ministry of electronics and information technology wasn’t immediately available for comment. “Without any proof, slandering a specific side is irresponsible behavior and an ill-intentioned one,” Chinese foreign ministry spokesman Wang Wenbin said in Beijing on Wednesday.
The intrusions into India’s critical infrastructure have been occurring since at least the middle of last year, according to Recorded Future, which tracks back to the start of a bloody skirmish between Indian and Chinese soldiers at a border post in the Himalayas.
Since then, authorities across India’s federal and state governments have been bickering about whether a cyberattack was responsible for the October collapse of the power grid that supplies Mumbai, an outage that brought the financial hub to a halt for several hours, impacting stock markets, transport networks and thousands of households.
Recorded Future, a privately held cybersecurity firm based near Boston that tracks malicious activity by nation-state actors, hasn’t made any connection or assertion between the traffic observed under RedEcho and the Mumbai outage. But, Solomon said, “it’s not unusual to see this type of technique used by nation states as an instrument of national power.”
“This could be as simple as trying to drive influence operations to be able to signal either to the people or the government that at any given time they have leverage that can be used against them,” he added.
Indian federal officials have denied that any cyberattack has occurred, but say malware was found. The National Critical Information Infrastructure Protection Centre emailed the central Power System Operation Corp about the threat from RedEcho on February 12, the power ministry said in a statement on Tuesday. Dispatch center employees shut down control functions that allow circuit breakers to be operated remotely. They changed user credentials and isolated vulnerable equipment.
Investigators from Maharashtra are due to present their findings to local lawmakers on Wednesday.
Regarding the Mumbai power outage of October 12, initial information suggested 14 Trojan Horses, that is malicious code, and 8 gigabyte of unaccounted foreign data could have been transferred to the main electricity board, Anil Deshmukh, Maharashtra state’s home minister, said in a briefing on Monday. He added that black-listed IP addresses had tried to log-in to the board’s servers. He didn’t attribute the attack to any country or entity.
The 10 entities RedEcho infiltrated account for nearly 80% of India’s land mass from an electricity-coverage perspective, Solomon said. The intrusions could have remained unexposed and undetected until they were needed as leverage, he said.
“If it was meant to take down the lights, it would have taken down the lights,” Solomon said. “It didn’t.”
10-power-assets, too-
Sanjay Dutta, March 3, 2021: The Times of India
From: Sanjay Dutta, March 3, 2021: The Times of India
10 power assets, Mumbai, Tamil Nadu ports came under RedEcho cyberattack
NEW DELHI: Cyber attacks by RedEcho, the actor group with China links, on India’s power infrastructure have been more widespread than previously known and the intrusive infrastructure remains active even after military de-escalation in Ladakh’s Pangong area.
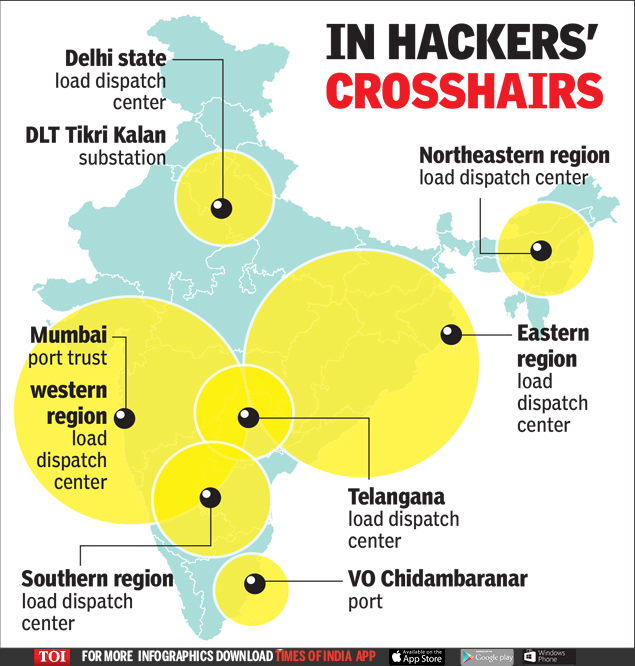
According to Christopher Ahlberg, CEO of Recorded Future, the Massachusetts-based enterprise security outfit that detected the intrusions, 10 Indian power sector assets and the Mumbai and Tamil Nadu’s VO Chidmabaranar ports came under attack.
The power assets that came under attack were Delhi state load despatch centre, DTL Tikri Kalan substation in Delhi; Mumbai Port Trust, western regional load despatch centre In Maharashtra, NTPC's Kudgi power plant and southern regional load despatch centre in Karnataka, VO Chidambarnar port in Tamil Nadu, Telengana load despatch centre, eastern regional load despatch centre in West Bengal load despatch centre and northeastern regional load despatch centre in Assam.
"Recorded Future observed through its network intelligence significant, high-volume, network traffic from Indian power sector assets to servers used by China-linked group RedEcho… The adversary infrastructure is still active and activity continues (even after Pangong pull-back announcement)," Ahlberg said in a presentation on the group’s findings.
Charity Wright of Insikt, Recorded Future’s threat research group, said the location of targeted infrastructure covered the length and breadth of India’s geography as well as the demography.
A New York Times report had last Sunday blown the lid off on these intrusions, citing findings by Recorded Future. It raised doubt Chinese hackers may have caused the October 12 power outage in Mumbai as a warning against strong Indian pushback to PLA’s border transgressions in Ladakh.
On the power ministry’s statement that no installation was affected as safeguards were already in place, Wright said it showed the government responded to alerts. On power minister RK Singh blaming the Mumbai blackout on human error, Ahlberg said there was insufficient data to prove cyberattack caused the Mumbai blackout.
Targeting the Indian energy sector offers limited economic espionage opportunities. But the group believed “gathering future operational activity, pre-positioning destructive malware, as a warning/show of force during heightened bilateral tensions; and potential information operation to disturb Indian population” could be the possible objectives.
Ahlberg said RedEcho “has overlapping modus-operandi with several Chinese groups, including APT41 and Tonto Team,” the known cyber threat groups that take directions from established nation-states to carry out cyberattacks.
Wright said her group detected the intrusions using large-scale automated analytics and analysis. These included a combination of proactively identifying adversary infrastructure through server fingerprinting; identifying established sessions between the victim and adversary infrastructure through network traffic analysis; and enriching traffic analysis with proprietary data sources for victim identification.
This was the same methodology used to detect power sector intrusions in the European transmission control system, ENTSO-E.
Indian vaccine makers
Chinese hackers target Indian vaccine makers Serum Institute, Bharat Biotech: Security firm
NEW DELHI: A Chinese state-backed hacking group has in recent weeks targeted the IT systems of two Indian vaccine makers whose coronavirus shots are being used in the country's immunisation campaign, cyber intelligence firm Cyfirma told Reuters.
Rivals China and India have both sold or gifted Covid-19 shots to many countries. India produces more than 60% of all vaccines sold in the world.
Goldman Sachs-backed Cyfirma, based in Singapore and Tokyo, said Chinese hacking group APT10, also known as Stone Panda, had identified gaps and vulnerabilities in the IT infrastructure and supply chain software of Bharat Biotech and the Serum Institute of India (SII), the world's largest vaccine maker.
"The real motivation here is actually exfiltrating intellectual property and getting competitive advantage over Indian pharmaceutical companies," said Cyfirma Chief Executive Kumar Ritesh, formerly a top cyber official with British foreign intelligence agency MI6.
He said APT10 was actively targeting SII, which is making the AstraZeneca vaccine for many countries and will soon start bulk-manufacturing Novavax shots.
"In the case of Serum Institute, they have found a number of their public servers running weak web servers, these are vulnerable web servers," Ritesh said, referring to the hackers.
"They have spoken about weak web application, they are also talking about weak content-management system. It's quite alarming." China's foreign ministry did not immediately reply to a request for comment.
SII and Bharat Biotech declined to comment. The government-run Indian Computer Emergency Response Team, with whom Cyfirma said it had shared its findings, had no immediate comment.
The US Department of Justice said in 2018 that APT10 had acted in association with the Chinese Ministry of State Security.
Microsoft said in November that it had detected cyber attacks from Russia and North Korea targeting Covid-19 vaccine companies in India, Canada, France, South Korea and the United States. North Korean hackers also tried to break into the systems of British drugmaker AstraZeneca, Reuters has reported.
Ritesh, whose firm follows the activities of some 750 cyber criminals and monitors nearly 2,000 hacking campaigns using a tool called decipher, said it was not yet clear what vaccine-related information APT10 may have accessed from the Indian companies.
Bharat Biotech's Covaxin shot, developed with the state-run Indian Council of Medical Research, will be exported to many countries, including Brazil.
US drugmaker Pfizer Inc and its German partner BioNTech SE said in December that documents related to development of their Covid-19 vaccine had been "unlawfully accessed" in a cyberattack on Europe's medicines regulator.
Relations between nuclear-armed neighbours China and India soured last June when 20 Indian and at least four Chinese soldiers were killed in a Himalayan border fight. Recent talks have eased tension.
2021, Mar: Red Echo hackers targeted NTPC infra
Anam Ajmal, March 10, 2021: The Times of India
China hackers targeted NTPC infra just days back: US outfit
New Delhi:
The intrusion into India’s power plant infrastructure by Chinese state-backed hacker group Red Echo continues. The last such activity was noticed as recently as February 28 and this was revealed on Tuesday at a webinar by US-based cyber security organisation Recorded Future, reports Anam Ajmal.
“We have observed significant, sustained, high-volume traffic from Indian power sector assets to Red Echo infrastructure... The Red Echo infrastructure is still active, with the last observation on February 28, with communication to NTPC infrastructure,” said Charity Wright, a researcher with Recorded Future’s threat analysis department, Insikt Group. After a malware is planted, the compromised system starts communicating with the hacker’s server. On March 1, the Massachusetts-based organisation had released a report about Red Echo attempts to “infiltrate” India’s power plants by planting a malware identified as ShadowPad in at least 10 power plants and two seaports.
As per Wright, Red Echo’s activity was first noticed in October 2020. Recorded Future informed the Indian government about the intrusion on October 10, just two days before a major power outage impacted Mumbai and surrounding areas. “We have been tracking their malicious infrastructure since October 2020. But there is no evidence to suggest that the Maharashtra state power plant failure was linked to Red Echo,” Wright said.
Cyber security experts in India said the rising instances of these intrusions are cause for concern. “We don’t know what system had been compromised; it could have been a harmless administrative server. This needs to be taken seriously as it could basically mean China is prepositioning itself in case (political) conditions deteriorate,” said cyber-politico expert Jiten Jain. “The government, going forward, has asserted that it will not use Chinese parts in sectors like power and telecom. But the existing infrastructure is flooded with Chinese parts. They pose a threat and nobody seems to be talking about that,” Jain said.
The intrusion, as per Wright, could not have led to any economic gains. “The group was preparing for future operations. They were basically communicating their capability to the adversary (India). By hiding in India’s (critical) infrastructure, they wanted to convey that they had control over Indian assets if they made another move (against China),” he said.